Twitter (X.com) bots and threats
I recently re-created a X (formerly known as Twitter, you’re learning nothing here) account after almost 2 years being off the platform. I wanted to have a new account to be able to follow what’s going on in wars in the M-E/Ukraine and what threat-actors and threats are emerging from them, this period being quite active with the new front opposing Liban’s Hezbollah and Iran to Israel.
This account is exclusively dedicated to following OSINT and CTI sources, as well as some news feeds. I don’t do any social interaction with this account, not even liking or reposting tweets (or whatever they are called now).
But what surprised me the most was how Twitter is being polluted with bots. After a few days on the platform, I have 20+ follower requests from random bots, most of them posing as women who fit the stereotypical European/North-American beauty standards.
What’s strange is that many of those bot accounts are simply… empty. From the 26 pending requests I currently have at the time of writing this, only 6 have a link in their bio, and 10 have at least one post. Some of them being pure feed for thought (r/im14andthisisdeep material):
Before continuing, please keep in mind that the following analysis will be done on a very small sample ($n=26$), so trends cannot be inferred with such a small study group.
Let’s focus on the links now. As stated before, only 6 accounts had a link somewhere in their bio. 3 of them are using an URL shortener (probably for tracking obfuscation?), and the 3 others are just using cheap TLD with the account handle in the URL.
// using URLs shortener
tinyurl[.]com/24amls4v
tinyurl[.]com/2ygbkjps
tinyurl[.]com/2xqu3txw
// using the X handle in the URL
rebekahjinkerson[.]click/ConstanceA74101
mamielournes[.]buzz/CopJewe
darylastry[.]sa[.]com/EmeldaGood43712
TinyURL
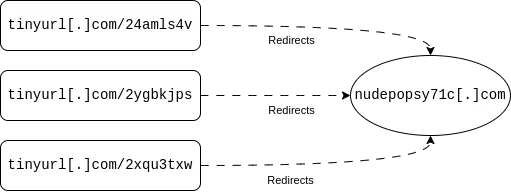
I first tried to reach all of the TinyURL links in a sandboxed environment. They all does a bunch of shady redirects to websites containing the original Twitter account handle in the URL, to finally end up on nudepopsy71c[.]com with a specific UTM parameter.
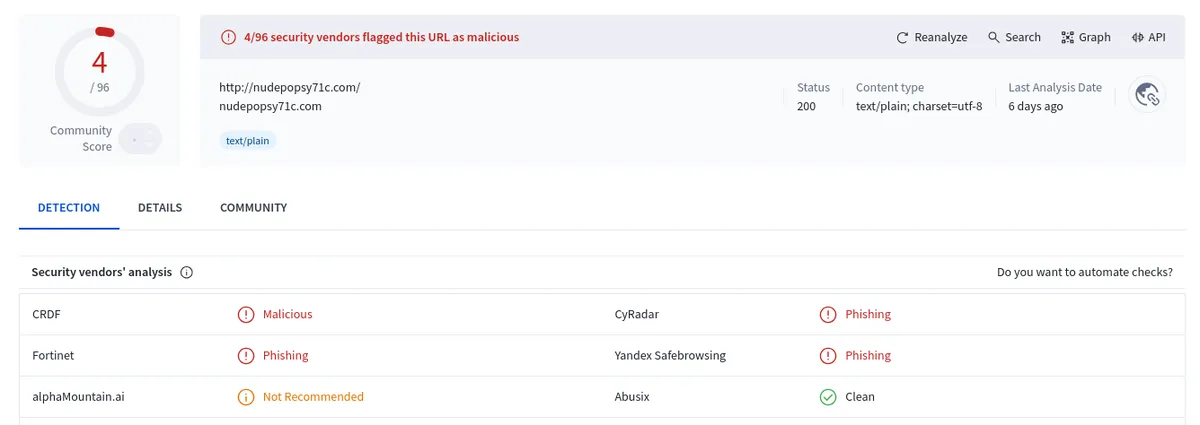
The website contains p0rn content and is flagged by VirusTotal as a adware/phishing site:
But without the right ?utm_source parameter, the site returns an empty webpage:
Once on the website, you have a basic form to fill to ensure you’re not a bot, and then you’re redirected to another online dating scam website which seems to vary depending on the visitor’s location (for me, it was a .fr domain but from what I read online, some ended up on .nl domains, etc.).
According to the WHOIS record, the domain has been booked less than a year ago and the nameservers are managed using Cloudflare, so the infrastructure is probably behind Cloudflare too:
$ whois nudepopsy71c[.]com
Domain Name: NUDEPOPSY71C[.]COM
Registry Domain ID: 2833075027_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.namesilo.com
Registrar URL: http://www.namesilo.com
Updated Date: 2024-02-20T12:25:00Z
Creation Date: 2023-11-27T11:42:47Z
Registry Expiry Date: 2024-11-27T11:42:47Z
Registrar: NameSilo, LLC
Name Server: ADDILYN.NS.CLOUDFLARE.COM
Name Server: GERALD.NS.CLOUDFLARE.COM
The latter can be confirmed by checking the IP address:
$ dig +short nudepopsy71c[.]com | xargs ipinfo
{
"ip": "188.114.96[.]2",
"anycast": true,
"city": "San Francisco",
"region": "California",
"country": "US",
"loc": "37.7621,-122.3971",
"org": "AS13335 Cloudflare, Inc.",
"postal": "94107",
"timezone": "America/Los_Angeles"
}
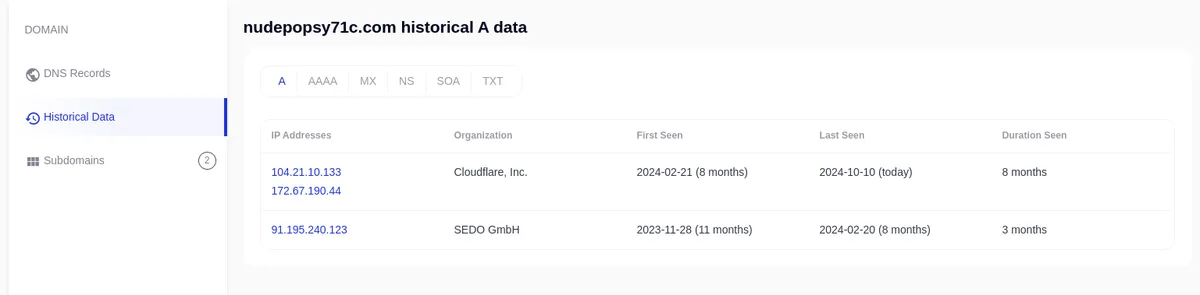
From there, we could think it’s over and call it a day, but hopefully there’s another path to dig in to try to gather more information about the target: passive DNS history. Doing some research, we can see that before being put behind Cloudflare, the domains responded to another IP address: 91.195.240[.]123, which also matches with the time the domain has been reserved (November 28th 2023 vs. November 27th 2023 for the domain registration):
$ ipinfo 91.195.240[.]123
{
"ip": "91.195.240[.]123",
"city": "Munich",
"region": "Bavaria",
"country": "DE",
"loc": "48.1374,11.5755",
"org": "AS47846 SEDO GmbH",
"postal": "80331",
"timezone": "Europe/Berlin"
}
However, SEDO GmbH being a marketplace for domain names, it’s possible that the domain got bought and stayed parked there until February 2024, when the owners deployed it behind Cloudflare directly.
Custom domains
This part will focus on the three remaining domains that are not using URL shorteners.
Two of the domains (rebekahjinkerson[.]click/ConstanceA74101 and mamielournes[.]buzz/CopJewe) returned me some 301 Moved Permanently and redirected me to the Google home page. It may seem pretty useless at first but that’s enough for the bad actors to know which Twitter handle worked and get some browser fingerprinting and information (IP address, user agent hence device info, etc.).
For darylastry[.]sa[.]com/EmeldaGood43712, it simply followed the same process as for the URL-shortened links and redirected me toward our well-knowned nudepopsy71c[.]com. Nothing new here.
Spray n’ pray
Why are so many obviously fake bots trying to follow me? And why don’t they even try to send a message or mention me in a tweet?
Those bots are propagating what’s called PIB scams, or P*ssy In Bio scams. The ultimate goal of those is to funnel victims through multiple websites to ultimately end on the final one that will ask for your credit card. Usually, the end sites are proposing services to chat with ““women”” (freelance operators in real life), and either asking for money for it or delaying the mention of money later in the discussion.
Even if it’s an obvious scam, if 0.1% of the targets (aka all Twitter users) fail to detect it and get trapped, it’s enough for scammers to make money without a lot of effort. If you wanna learn more about this scheme, I found out this article while doing my research, which explains the topic well.